Many designers have heard of zigbee and the IEEE 802.15.4 standard, but it is unclear whether they should choose zigbee or 802.15.4, or develop their own proprietary network protocols. This article will use a proprietary protocol as an example to introduce the advantages of various protocols and to make a comparative distinction between performance and application areas. Discuss different network topologies, resource requirements, and flexible features to help interested parties choose the development protocol that best suits their application needs.
This article is divided into three sections about low-power networks and how to choose between them. The first part discusses network basics and low-power network selection criteria; the second part continues to explore selection criteria and introduces the 802.15.4 protocol; the third part introduces zigbee and the proprietary network protocol SimpliciTI, and measures these protocols according to the above selection criteria.
first part
One of the most important trends in the electronics market is that more and more products are beginning to add wireless connectivity. Various products such as water and electricity meters, home security systems, TV remote control or fitness equipment have added wireless connection function. This aspect is convenient for users to use. Users can control anywhere in the room by wireless remote control, unlike infrared remote control. The aiming device can only work; on the other hand, this wireless control is also to reduce the expensive cost of room rewiring, such as installing a home security system without rewiring. In addition, devices such as Automatic Meter Reading System (AMR) or Advanced Metering Architecture (AMI) are increasingly relying on low-power protocols to make devices last for years.
This article will provide an overview of wireless network protocols, but will focus on the zigbee and 802.15.4 protocols and compare them to proprietary network protocols that are designed to meet the requirements of low-power applications. Although many engineers are familiar with these network protocols, they may not have been carefully evaluated. Even if someone has evaluated these protocols, it may not be clear which protocol is most appropriate for a particular application. This article is divided into three parts. In the first part, we will introduce the basics of networking, including common network terminology, Open Systems Interconnection (OSI) network models, etc., and explore the factors that should be considered when selecting a network for a particular application; the second part, we will give A series of network selection criteria, based on these standards to compare the three network protocols; the third part, we will detail the 802.15.4, zigbee and SimpliciTI proprietary network protocols, and give specific examples of how to determine the appropriate according to the selection criteria The best network protocol for a particular application.
At present, there are many types of wireless network protocols introduced. Below we only list some of the network protocols:
Standardized protocols such as WiFi (802.11b), Bluetooth, zigbee, zigbee Pro, 802.15.4, RFID, and Wireless USB.
The proprietary protocol introduced by chip manufacturers, third parties, etc., is referred to herein as the "DIY" network protocol and is only used in products produced by companies that have introduced the agreement.
Figure 1 shows various network protocols and their key application areas and typical resource requirements. When comparing low-power protocols (such as zigbee/802.15.4 with other protocols), we should focus on some key features that distinguish low-power wireless networks from other networks, such as low data rates, short connection distances, and low frame overhead. The complexity is low, and there is the power management requirements of the protocol itself. The above design factors are all for the purpose of reducing the power consumption of the network unit nodes. As shown in Figure 1, the zigbee/802.15.4 protocol is ideally suited for applications in the environmental monitoring market, ensuring that battery-powered devices work best for long periods of time and are comparable to hardware that supports larger, more complex protocols. It can also effectively reduce costs.
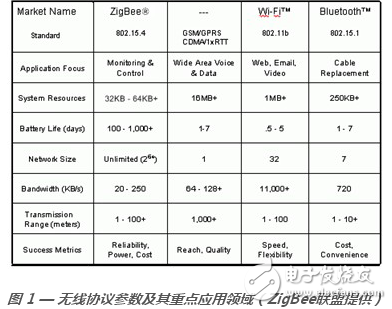
Low-power networks are primarily designed to provide wireless connectivity between battery-powered devices that last for months or years. In most low-power wireless systems, sending and receiving data over the air is the most power consuming. Therefore, we should minimize the power consumption of the radio, which is essential for extending battery life. Since the distance between signal transmission and reception is proportional to the power input of the antenna, the coverage of the wireless network between different nodes is generally limited. Wireless protocols should also reduce their complexity to reduce computational overhead and avoid the use of large amounts of memory, thereby reducing costs.
Network basics
Figure 2 shows a block diagram of a typical low-power network node. Typically, one or more sensors in a node are responsible for collecting data or status and/or providing a user interface to the system. The microcontroller is connected to the sensor and controls the radio (in this case CC1100 or CC2500), while the radio is responsible for the transmission and reception status.
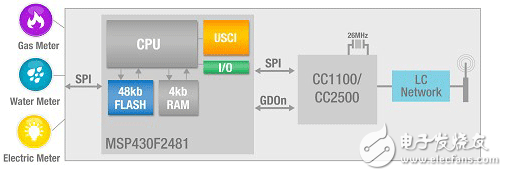
Figure 2 – Typical Low Power Network Block Diagram (This example shows an automatic meter reading system application)
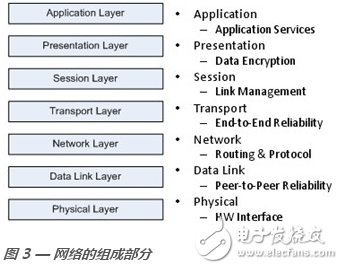
Whether it is a wired network or a wireless network, we can conceptually consider network node communication as the Network Open System Interconnection (OSI) basic reference model as shown in Figure 3. This model was developed by the International Organization for Standardization (ISO) in the late 1970s, which divided the network protocol implementation components into different software layers. For two applications on different devices to communicate, the message must pass through the application layer and go through the physical layer to the other side. Each layer can only communicate with its neighbors.
How to understand the layered software architecture? We can imagine the process of sending a letter. The letter itself is equivalent to the application data. We put the letter in the mailbox, waited for the postman to take it out, and then get it to the post office. The post office sorts all the letters according to the address of the addressee and then sends the letters to the final destination by air, sea or land. In order for the letter to reach the recipient's hands, the post office on the recipient's side must also go through the reverse set of procedures, first to the post office where the addressee is located, sorted by destination, and then sent to the recipient's mailbox, and finally reach the letter. In the hands of people. The mailing process actually reflects a four-layer communication protocol. The first letter is the letter, and the local post office is the second floor. The post office classifies the letter as the third floor, while the letter transport mode is the fourth floor. Each layer has its own tasks and is only related to adjacent layers. The letter can only be transmitted from one end of the whole link to the other end, and the content (or application data) of the letter can be successfully exchanged between the two parties.
The OSI model involves seven different software layers. The application layer is an interface directly to the user. The presentation layer formats the message into the format of the incoming and outgoing network, usually embodied as message encryption and/or encoding. The session layer creates and manages logical links between any two devices on the network. The transport layer is responsible for providing reliable end-to-end communication. If the fault of the transport layer is too frequent, the channel noise may be too large, or the quality of the link itself is not good, then the session layer is notified to establish a new link between the failed nodes. The network layer is responsible for the network routing mechanism, and the message transmission between different devices is the responsibility of the data link layer. The data link layer ensures that the message is delivered point-to-point, but the actual transmission of the message on the physical medium is the responsibility of the physical layer. In this way, messages can be transmitted from one end of the OSI model to the other.
Designers can choose to implement different numbers of layers of protocols and can customize other layers depending on the application needs. At present, most network implementations cannot actually implement all layers completely, and some functions of certain layers need to be mixed according to the requirements of the protocol. In fact, the OSI model is the best framework for understanding the complexity and different functions of the protocol architecture. Designers should understand which functions are implemented in their own solution and which functions can be ignored.
To determine exactly which wireless protocol to choose among zigbee, 802.15.4, and proprietary networks, we list some selection criteria:
Application considerations
Robustness and reliability
Easy to use
Hardware and RF considerations
Below we will discuss the above criteria in detail.
Application considerations
The initial steps of network design, like any other system design effort, are high-level requirements for defining an application. Below we list some of the most important network parameters, which should be clearly defined before determining any wireless protocol as a final solution. We will then present possible implementations in accordance with these standards in this article, and these selection criteria and protocols themselves will be further elaborated.
Network topology
How many nodes does the application need? What kind of basic organization form does the node take?
Communication reliability
How important is the network for receiving each packet?
Network security
Does the data need to be secure? How important is the absolute security of network data transmission if needed?
Customization and design flexibility
To what extent does the network protocol solution need to be customized to meet the application requirements, and does the protocol provide an unconstrained design?
Development time and protocol complexity
This article is closely related to item 4, and how complex is the agreement itself?
Interoperability
Does interoperability with other vendors' technologies benefit the end product? Will the final product become a completely proprietary solution?
Figure 4 shows the four most common wireless network topology implementations.
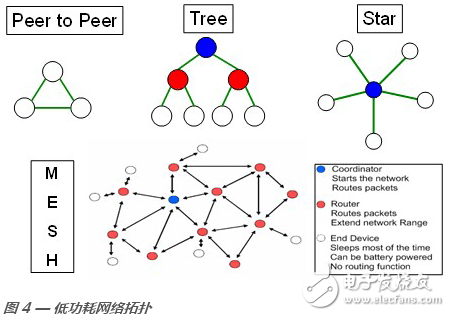
A peer-to-peer network topology supports one-way or two-way links between different nodes on the network. Only nodes that are within range of the connection will communicate with each other because maintaining a direct physical link is a necessary condition for their communication; the only exception is a broadcast message, which can be broadcast over the network. In a tree network topology, each network node is associated with its parent node, and network addressing also reflects this node relationship, which is very similar to an IP Internet address. In this way, we can implement a more efficient routing algorithm because more node network address bits can reflect the relationship of a node relative to its peer. A star network can treat a single node as a network coordination point and is responsible for various possible network management control tasks, such as node association, node network join and link permissions, message forwarding, and secure exchange. The star network relies on coordination points to maintain network communication. If there is a problem with the coordination node, network communication will also be affected.
In the most basic sense, a mesh network is a network with at least two connection paths per node. A full mesh network means that each node has a direct connection to other nodes. A full mesh network is unreasonable in many cases, as it will soon limit the network size to the smallest network covered by the weakest connected devices, and the mesh network requirements are too strict. However, people will find some kind of compromise between the two situations, launch a network through a central node, use tree addressing technology to locate nodes and manage the relationship between nodes. A range extender, also known as a routing node, can send messages on the network. If a node or coordination node has a problem, the network can continue to work normally, but it will affect the operability to some extent. Other excellent features such as self-healing route discovery and route expiration can improve the reliability and efficiency of routing algorithms.
Another important factor to consider is the financial costs involved in using a protocol. The use of proprietary network protocols provided by an organization generally requires payment of membership fees or royalties. However, there is no need to pay royalties for using zigbee, but it is required to join the alliance and pay a nominal membership fee each year. In addition, the verification process also requires a lot of time and money. A proprietary protocol from a chip manufacturer typically requires that its products be used only at its licensed location.
Robustness and reliability
The robustness and reliability of low-power network protocol implementation can be attributed to three points: message delivery, physical layer considerations, and messaging protocols. Message delivery depends on routing technology to ensure the successful transmission of data packets and the security of network transactions. Physical layer considerations involve interference with noise or other transmitted signals within the working channel. The messaging protocol defines the partitioning of the channel, ensuring that all devices can use physical media without causing packet collisions during transmission. All of the above three points contribute to improving network service quality (QOS), which is a series of network standards for measuring packet communication efficiency, transmission rate and failure rate.
Channel scanning is the ability to listen for the amount of transmission or noise in a channel and is a physical layer consideration. The network protocol uses channel scanning to find the channel within a particular operating frequency band that is least likely to interfere with inter-node communication. Frequency agility refers to the ability of a network to change the working channel of all nodes on the network, so that even if a channel is interfered, the network can continue to work. We can also improve the message delivery capability through the confirmation mechanism, that is, let the receiving node feed back an ACK confirmation message to the original sending node after successfully receiving the data packet. The peer-to-peer confirmation mechanism in conjunction with the definition of the number of message retries helps to significantly reduce the possibility of packet loss. The end-to-end acknowledgment mechanism will provide another layer of security to ensure that packets are not lost, which is especially important in large multi-hop networks with complex routing algorithms.
The messaging protocol defines how network bandwidth is obtained and partitioned. Different wireless protocols may define different bandwidth partitions, which may include frequency division, space division, time division, or code division. Frequency division can be understood as a room with people talking in different voices; air points can be understood as a room for people to talk in different directions; time can be understood as a room where people compete for the right to speak, but as long as one person preemptively speaks, others People no longer speak; code points can be understood as a room for people to speak different languages ​​with different voices. Only the time division, that is, the time division multiple access protocol, is discussed in the protocol referred to herein. This protocol has two possible implementations of synchronous and asynchronous communication.
The coordinating node broadcasts periodic network beacons and divides the time intervals between different beacons into the same time slot, thereby implementing synchronous communication. A single network beacon and each time slot that appears before the next beacon is referred to as a superframe. The time slots of the superframe can be further divided into active and inactive communication periods, so that the coordination node can enter the sleep state in the low power mode of the inactive period. We can ensure or allow parties to contend for time slots through Channel Sense Multiple Access (CSMA) technology or pre-communication listening algorithms.
The CSMA algorithm defines the protocol used by the arbitrating RF channel when multiple nodes attempt to communicate at the same time. The most common implementation is to use the CSMA/CA algorithm, where the CA refers to the anti-collision system because the sending node will cancel the sending of the message once it hears that the channel is busy. There are other implementations of the CSMA algorithm, such as CSMA/CD (collision detection) and CSMA/CR (collision resolution), but these are not common in RF protocol implementation and are not within the scope of this article.
Security is another important factor affecting the robustness of wireless communications, and it is also the main function of the network. For example, a home security network might include a garage door opener that can be used to switch garage door locks. Such systems need to be highly secure to prevent eavesdropping or security breaches and to ensure privacy. We can ensure security by using different levels of security keys and encryption mechanisms, message authentication and integrity protection, and using a secure trust center, that is, through a single node on the network (usually Network coordination nodes) instead of using distributed security mechanisms to solve all security problems. If a distributed security mechanism is adopted, symmetric keys are exchanged when different links are created. An attack node bypasses the direct authentication of the management node and can easily enter the network.
2Ml Refillable Vape Pen,Veiik Disposable Vape Pen,Disposable Vape Stick,Disposable Vape Pens
Shenzhen Wanna Technology Co.Ltd , https://www.veiikvape.com