In order to ensure the correctness and integrity of the data transmission during the communication process, and in the communication process, if a single bit error occurs in the data transmission, it can be corrected, and the information data is encoded by Hamming and then transmitted.
The Hamming Code, also known as Hamming Code, was invented by Richard Hamming in 1950. The Hamming code also uses the concept of parity to verify the validity of the data by adding bits after the data bits. Therefore, Hamming code also belongs to linear error correction code (error-correctable 1-bit error detection 2-bit error). Hamming code cannot achieve 2 or more digits of error correction.
Hamming code principleHamming code operations need to construct G generation matrix and H supervised matrix. For the construction method, please refer to the related computer principle books. Here, you only need to understand some simple concepts.
Let the number of data bits be m and the number of check digits be k, then the total number of coded bits is n, so, n=m+k, then,
There is Hamming inequality:
2^k-1》=n
It can also be expressed as: 2^k"=m+k+1. This inequality is used to compare the number of data bits and the number of check bits. For example, if the data bit is 64, then the check digit is ("2^ Kk"=65" = "k=7).
The number of check digits generally refers to the minimum value, because the smaller the k, the smaller the total information bits, and the smaller the transmission overhead.
The number of information bits generally refers to the maximum value, but since 2^kk can only take values ​​in fixed discrete values, the information bits may not be the maximum value. For example, the information bit is 24, and the calculation requires parity bit 5, but the same information. When the bit is 25, the parity bit is also 5.
The number of check digits vs. information digits is as follows:
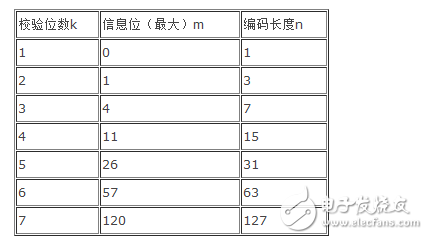
Note: The characteristics of Hamming code determine that generally do not do too many information bits to verify, the longer the information bit, the higher the probability of having two more errors, which will bring the difficulty of error correction.
Hamming code coding principleThe code length is n, the information bit length is k, and the supervision bit length is r=nk. If you need to correct a bit error, because each bit in the sequence of length n may be wrong, there are n cases, and there is no error, so we must use the supervised code of length r to represent n+1. Kind of situation. The supervisory code of length r can represent 2^r cases in total. therefore
2^r 》= n + 1, ie r ′= log(n+1)
Let us illustrate the Hamming code with an example. Assuming k=4, you need to correct a single error, then
2^r 》= n + 1 = k + r + 1 = 4 + r + 1
Solve r 》= 3. Let us take r=3, then the code length is 3+4=7. Use a6, a5,. . .a0 represents these 7 symbols. The syndromes in the three supervisory relationships are represented by S1, S2, and S3. We make the following provisions (this rule is arbitrary):
S1 S2 S3 error code location
0 0 1 a0
0 1 0 a1
1 0 0 a2
0 1 1 a3
1 0 1 a4
1 1 0 a5
1 1 1 a6
0 0 0 No error
According to the regulations in the table, the syndrome S1 is 1 only when an error code position is at a2, a4, a5 or a6, otherwise S1 is 0. This means that the four symbols a2, a4, a5, and a6 form an even parity relationship:
S1 = a6⊕a5⊕a4⊕a2 (1)
In the same way, you can get:
S2 = a6⊕a5⊕a3⊕a1 (2)
S3 = a6⊕a4⊕a3⊕a0 (3)
When transmitting a signal, the value of information bits a6, a5, a4, a3 depends on the input signal and is random. The supervision is a2, a1, a0 should be determined according to the value of the information bit according to the supervisory relationship, that is, the value of the supervisory position should be such that S1, S2, and S3 in the above formula (1)(2)(3) are 0, which means There is no error code in the initial situation. which is
A6⊕a5⊕a4⊕a2 = 0
A6⊕a5⊕a3⊕a1 = 0
A6⊕a4⊕a3⊕a0 = 0
The shift operation is performed by the above formula to obtain:
A2 = a6⊕a5⊕a4
A1 = a6⊕a5⊕a3
A0 = a6⊕a4⊕a3
After the information bit is known, the values ​​of the three supervisory bits a2, a1, and a0 can be calculated according to the above formula.
After receiving the code group, the receiver first calculates S1, S2, and S3 according to the formulas (1) to (3), and then checks the table to know the error code.
For example, if the received codeword is 0000011, it is calculated according to (1)~(3):
S1 = 0, S2 = 1, S3 = 1
Look up the table to get a wrong code in the a3 bit.
The minimum Hamming distance of this encoding method is d=3, so this encoding can correct one error code or detect two error codes.
Hamming code instanceThe following example is the (30, 24) Hamming code calculation method used in the MIPI Alliance Specification for Display Serial Interface (Chapter 9). The DSI header format is fixed to 24bits Data+8bits ECC, and the 8bitsECC is preset to P6=P7. =0, so the actual n = 30, m = 24, k = 6.
The test bit calculation method refers to the MIPI DSI table 22 generation matrix (Px vs [DataBit0~DataBitx]), such as P5=D10^D11^. . .D23, indicating the corresponding P5 column of DataBit23, only these DataBit bits are 1.
Int main() {
Char res;
Char in[20]={0};
Char D0, D1, D2, D3, D4, D5, D6, D7, D8, D9, D10, D11, D12, D13, D14, D15, D16, D17, D18, D19, D20, D21, D22, D23;
Char P0, P1, P2, P3, P4, P5, P6, P7;
Cout ""Checking Codes(eg.0x1234AF, \"-\" for exit): 0x";
Cin》in;
If(in[0]=='-') {
Return 0;
}
For(int i=0;i"6;i++){
If((in[i]"='0') && (in[i]"='9')) {
In[i] = in[i]-0x30;
}else if((in[i]"='A') && (in[i]"='F')){
In[i] = in[i]-'A'+10;
}else {
Return 0;
}
}
D0=in[1]&0x01; D1=(in[1]&0x02)》》1;
D2=(in[1]&0x04)》》2; D3=(in[1]&0x08)》》3;
D4=in[0]&0x01; D5=(in[0]&0x02)》》1;
D6=(in[0]&0x04)》》2; D7=(in[0]&0x08)》》3;
D8=in[3]&0x01; D9=(in[3]&0x02)》》1;
D10=(in[3]&0x04)》》2; D11=(in[3]&0x08)》》3;
D12=in[2]&0x01; D13=(in[2]&0x02)》》1;
D14=(in[2]&0x04)》》2; D15=(in[2]&0x08)》》3;
D16=in[5]&0x01; D17=(in[5]&0x02)》》1;
D18=(in[5]&0x04)》》2; D19=(in[5]&0x08)》》3;
D20=in[4]&0x01; D21=(in[4]&0x02)》1;
D22=(in[4]&0x04)》》2; D23=(in[4]&0x08)》》3;
P7=0;
P6=0;
P5=D10^D11^D12^D13^D14^D15^D16^D17^D18^D19^D21^D22^D23;
P4=D4^D5^D6^D7^D8^D9^D16^D17^D18^D19^D20^D22^D23;
P3=D1^D2^D3^D7^D8^D9^D13^D14^D15^D19^D20^D21^D23;
P2=D0^D2^D3^D5^D6^D9^D11^D12^D15^D18^D20^D21^D22;
P1=D0^D1^D3^D4^D6^D8^D10^D12^D14^D17^D20^D21^D22^D23;
P0=D0^D1^D2^D4^D5^D7^D10^D11^D13^D16^D20^D21^D22^D23;
Res = ((P7&0x01)*8+(P6&0x01)*4+(P5&0x01)*2+(P4&0x01))*16+(P3&0x01)*8+(P2&0x01)*4+(P1&0x01)*2+(P0&0x01);
Printf("Result:0x%02X",res);
Return 0;
}
360 Laptop
360 laptop sometimes is also called as Yoga Laptop , cause usually has touch screen features. Therefore you can see other names at market, like 360 flip laptop, 360 Touch Screen Laptop,360 degree rotating laptop, etc. What `s the 360 laptop price? Comparing with intel yoga laptop. Usually price is similar, but could be much cheaper if clients can accept tablet 2 In 1 Laptop with keyboard. Except yoga type, the most competitive model for Hope project or business project is that 14 inch celeron n4020 4GB 64GB Student Laptop or 15.6 inch intel celeron business laptop or Gaming Laptop . There fore, just share the basic parameters, like size, processor, memory, storage, battery, application scenarios, SSD or SSD plus HDD, two enter buttons or one is also ok, if special requirements, oem service, etc. Then can provide the most suitable solution in 1 to 2 working days. Will try our best to support you.
To make client start business more easier and extend marker much quickly, issue that only 100pcs can mark client`s logo on laptop, Mini PC , All In One PC, etc. Also can deal by insurance order to first cooperation.
360 Laptop,360 Laptop Price,360 Flip Laptop,360 Touch Screen Laptop,360 Degree Rotating Laptop
Henan Shuyi Electronics Co., Ltd. , https://www.shuyielectronics.com